https://www.preemptive.com/blog/article/827-get-this-development-question-wrong-and-you-may-well-be-at-risk/91-dotfuscator-ce
Question: True or False, Seat belts are to Driver Safety as Obfuscation is to Application Risk Management
The correct answer is FALSE!
The equivalence fails because a seat belt is a device and obfuscation is a control. Why might you (or the application stakeholders) be in danger? First, read through the key descriptors of these two controls.
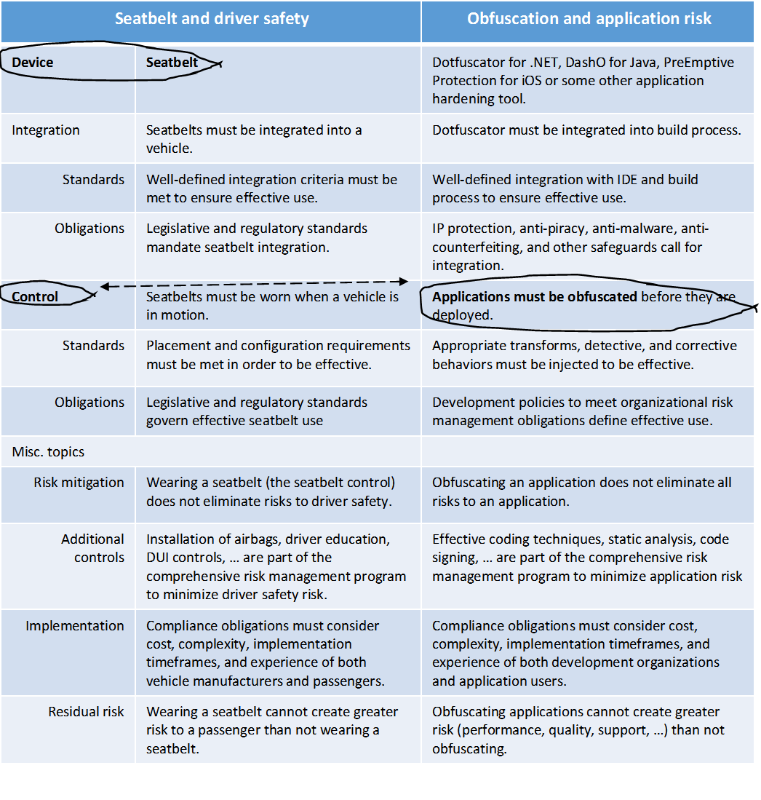
Table 1: contrasting application risk management with driver safety risk management.
To pursue application development opportunities as aggressively as possible (but not too aggressively to create unnecessary risk), organizations must also manage application threats and risks through a mix of proactive, detective and responsive controls;controls that are, in an ideal scenario, supported by strong analytics and based on strategic objectives, risk appetite and capacity.
If your organization has not settled on objectives, organizational risk tolerance, and what levels of investment you’re prepared to make to achieve these objectives, you can’t possibly have an effective risk management program.
Effective application risk management;
Consistency and efficiency requires sustained investments in the following:
Implement an effective feature set aligned with control categories (proactive, detective, and responsive).
Effective risk management supports all three control “dimensions.”
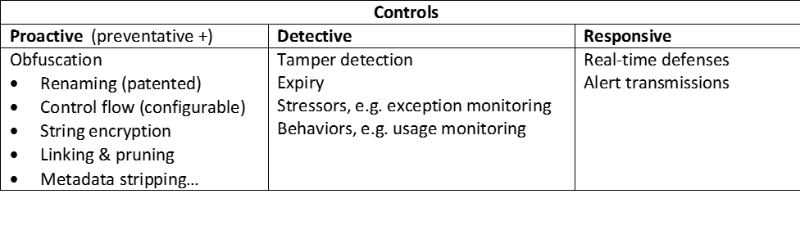
Table 2: Mapping of application hardening features to three categories of control.
This is not an exhaustive list of techniques and technologies to secure applications; and feature “bake-offs” are always suspect. However, if you don’t assess your risk (which has nothing to do with how easy it is to exploit an application vulnerability), you won’t know if a normal 3 point seat belt is sufficient (for a mainstream car) or if you need a child seat or a 5 point harness required by NASCAR.
Quality
As “the last step” before digital signing and application distribution, quality issues that may arise have the potential to have catastrophic impact on deployment and production application service levels.
Timeliness
Three factors drive release cycles for PreEmptive Solutions application protection and risk management products; the latter two are unique to the larger security and risk management category.
- New product features and accrued bug fixes: this is typically the sole driving force for new software product releases.
- Updates to OS, runtime, and specialized runtime frameworks: delayed support for new formats and semantics would result in delays in developer support for those platforms or will force poor risk management practices on the platforms that most likely need protection most of all.
- Emergence of new threats and malicious patterns and practices: as with anti-virus software, bad actors are constantly searching for ways to circumvent security controls. Without consistent tracking of this activity and timely updates to react to these developments, application security technology can quickly be rendered as obsolete.
Low friction
In order to be effective and consistently applied, the configuration and implementation of proactive, detective, and corrective controls cannot require excessive time or expertise. Specific areas where PreEmptive Solutions invests to reduce development and operational friction include:
- Automated detection and protection of common programming frameworks, e.g. WPF, Universal Applications, Spring, etc.
- Custom rule definition language to maximize protection across complex programming patterns at scale.
- Specialized utilities to simplify debugging of hardening applications.
- Automated deployment: support for build farms, dynamically constructed virtual machines, command line integration, MSBuild, Ant, etc. come standard with PreEmptive Solutions’ professional SKUs.
- Cross-assembly hardening to extend protection strategies across distributed components and for components built in different locations and at different times.
- Support for patch and incremental hardening to minimize and simplify updates to hardened application components.
Responsive support
Should critical issues arise, live support can prove to be the difference between applications shipping on time or suffering last-minute and unplanned delays.
Vendor viability
Applications can live in production for years – and with extended application lifecycles comes the requirement to secure these applications across evolving threat patterns, runtime environments, and compliance obligations.
No comments:
Post a Comment